Today we got an email from our Internet provider that we seem to attack an IP address within the provider’s network. Seemed to attack port 53. They ask us to check for viruses etc. The provider is Japanese, so the email was naturally Japanese too. Did not make it easier to understand for me.
Everyone knows, port 53 is DNS. Why would we or a virus try to connect port 53 on a non-server?
I checked all computers (the Windows machines was a natural first suspect), but all was clean. And then it dawned me: DNS Amplification attack! Using our router.
A quick check on the router showed more activity than normal, so it was confirmed that the router is the culprit.
The NAT connection table then promptly showed about 2000 connections with more and more being created while old ones were closed due to inactivity.
How to fix this? Disable remote DNS requests! Except remote is anything non-local to the router which also disabled the internal network from using DNS as all machines in our LAN use our router as DNS server (resp. relay).
The next attempt was better: set up the firewall to drop incoming DNS requests which come from the ppp interfaces.
Now I got about 50 active connections again (that’s normal), no odd DNS requests, and 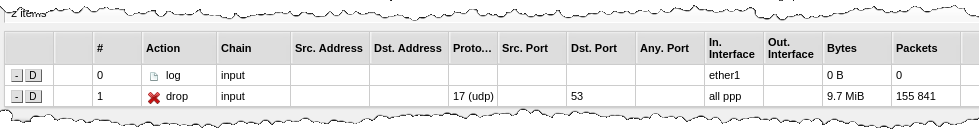 about 500 packets per second are being dropped. That accumulates quite fast. 280k packets dropped while writing this article.
about 500 packets per second are being dropped. That accumulates quite fast. 280k packets dropped while writing this article.
The magic fix looks like this:
/ip firewall filter add chain=input action=drop protocol=udp in-interface=all-ppp dst-port=53 log=yes log-prefix=Ext-Incoming-DNS
That was interesting. Relatively easy to defeat. I’m surprised this is not configured by default, but then, I have a rather non-user-oriented router where it’s expected that the admin knows what he’s doing…
I’ll have to look a bit more into security of the router in regards to DoS attacks and logging and notifications for unusual traffic.